Bots are becoming sophisticated and more human-like every passing day. And with the emergence of AI, it is becoming a dominant force for shaping online traffic.
According to Imperva BadBot Report 2025, 51% of the internet traffic is driven by bots, which is further amplifying with the introduction of AI and LLM. Unlike the basic bot traffic showing abnormal signs like high number of clicks/installs etc., the sophisticated bots can mimic human behaviour, therefore bypassing the validation checks.
As a precautionary measure and to check if your campaigns are impacted by bots/invalid traffic, there are signs that you can look for in your campaign data.
One of them being Click to Install Time to identify invalid installs in your mobile app campaigns.
In this blog we will breakdown how CTIT can be seen as a signal to identify invalid traffic and how marketers can use it to take proactive action against mobile ad fraud.
What is Click to Install Time? How to Identify Invalid Traffic Evaluating CTIT?
Let’s simply breakdown what CTIT means before moving forward to understand the kind of patterns that reveal exploitation of mobile ad fraud and click to install time.
Click Time: The moment a user clicks on your ad.
Install Time: When the app actually finishes installing.
Click-to-Install Time (CTIT): The time gap between these two.
It is basically a metric used in mobile advertising to map the time it takes for a normal user to download an app after clicking on an ad.
This gap varies naturally. Real users don’t install apps instantly every time; there can be delays, pauses, network differences, and human behaviour involved.
What a genuine user’s install journey looks like
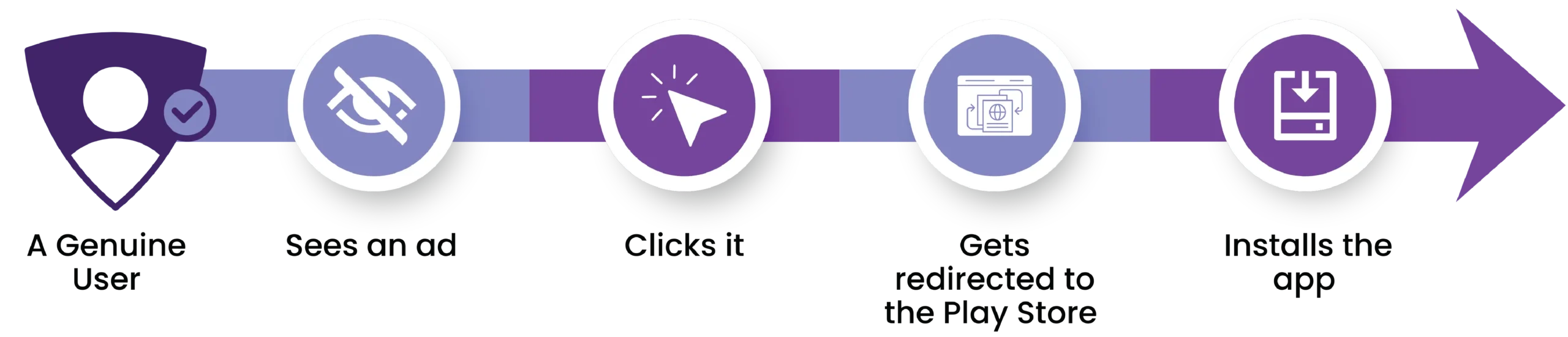
This process takes time, usually a few seconds to a few minutes, depending on network speed and app size.
However, fake installs show different timing patterns.
Here’s are the two types of abnormal CTIT patterns we observed recently that clearly indicate towards install fraud:
Examples of Abnormal CTIT Patterns
Case 1: Extremely short click-to-install time (click injection)

This snapshot compares the click time and install time for multiple installs coming from the same publisher. The gap between click and install is consistently just 1–3 seconds, and in several cases, the values are identical or nearly identical.
Why it is a problem?
A real user cannot click an ad, get redirected to the Play Store, download the app, complete the installation, all within a few seconds, repeatedly.
This pattern strongly indicates click injection, where fraudsters:
- Detect that an app install is already in progress
- Inject a click at the last possible moment
- Steal attribution credit for a genuine install
mFilterIt insight: Why this matters?
Although these installs appear valid in attribution reports, the timing exposes manipulation. Extremely short and repeated click-to-install times are a strong indicator of high-risk fake attribution, not real user engagement.
Learn more about common techniques of install fraud here.
Case 2: Google Play install begins before the user clicked on an ad
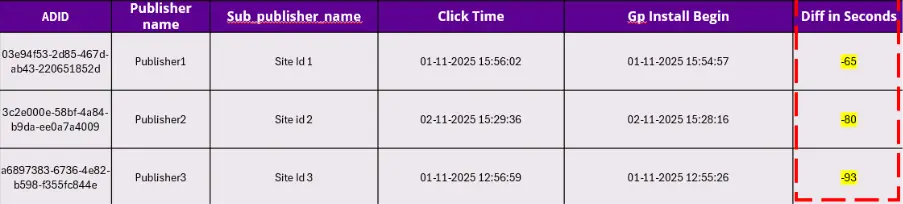
In this snapshot, the timestamps reveal something even more concerning. The Google Play install begin time occurs before the recorded ad click time. This results in a negative click-to-install time, meaning the install process started before the user supposedly clicked on the ad.
Why is it a problem?
This breaks the basic logic of attribution. A real user cannot start installing an app first and then click an ad for the same app afterward. When install activity precedes the click, it clearly indicates:
- Manipulated or falsified timestamps
- SDK tampering or fabricated attribution signals
This is not caused by reporting delays or tracking errors; it points to deliberate attribution manipulation.
mFilterIt insight: Why this matters?
Any case where the install begins before the ad click should be treated as install fraud by default. These patterns strongly indicate fake attribution attempts, even if the installs are being credited by attribution platforms.
Signs to Identify Abnormal CTIT Patterns
CTIT mapping should be approached in two layers: what you can validate manually and what requires advanced detection at scale.
As an advertiser, the following click to install time red flags should immediately raise concern, especially when they appear repeatedly.
Installs within 1–3 seconds of a click
Real users need time to reach the app store, download the app, and complete installation. Consistently instant installs are not normal human behaviour patterns.
Identical CTIT values across multiple installs
Human actions vary. When multiple installs show the same or near-identical timing, it often points to automated or scripted activity.
Long delays followed by sudden attribution
This pattern is commonly associated with click spamming, where random clicks are generated and later receive credit when an install happens.
Negative CTIT values
If an install begins before the recorded ad click, it breaks basic attribution logic and strongly indicates manipulated timestamps or fake signals.
How Advanced Mobile Ad Fraud Detection Solutions Help
Mobile ad fraud is often distributed across campaigns, publishers, and devices, making it difficult to detect without advanced analysis.
Attribution platforms answer one primary question: Who gets credit for the install? They do not answer whether the install journey itself was genuine or a fake one. While they work on assigning credits rather than behavioural validation, brands need an advanced mobile ad fraud detection solution to ensure campaign efficiency. Here’s how it helps:
Source-Level CTIT Pattern Analysis – Know who is installing your app
Advanced solutions analyze click-to-install time across all campaigns and channels simultaneously. This makes it easier to spot publishers or sources that consistently show unnaturally fast or uniform CTIT patterns. It also helps identify install fraud patterns that may look normal in isolation but become obvious when viewed across the entire account.
Analysis of CTIT with Click Behaviour – Don’t let sophisticated bots slip by
Click-to-install time is evaluated alongside click signals such as click frequency, burst patterns, and timing alignment. This helps distinguish genuine user clicks from injected or spammed ones.
Correlation with Device and Environment Signals – Differentiate between bot & human
Advanced solutions connect CTIT patterns with device-level indicators, including abnormal device reuse, emulator signals, or inconsistent environment data, strengthening fraud confidence.
Post-Install Behavior Validation – Protect your Bottom of the Funnel
CTIT is also checked against what users do post-install such as session depth, engagement, and conversion behaviour. Legitimate installs behave differently after installation than fraud-driven ones.
Continuous Learning and Pattern Evolution – Don’t stop at one signal
As fraud tactics evolve, advanced systems continuously learn from new timing patterns, ensuring detection stays effective even as attackers adapt.
How mFilterIt’s Mobile Ad Fraud Solution Helps in Proactive Detection
mFilterIt’s mobile ad fraud detection solution enables advertisers to identify, validate, and act on signals that CTIT mapping highlights. It analyses click-to-install time across campaigns and sources, click behaviour, and post install activity based on various parameters.
Based on this analysis, it helps advertisers’ flag and proactively block suspicious sources to prevent fraud from entering the campaign data. This ensures optimization decisions are driven by genuine user behaviour, not manipulated timing. By filtering out fraudulent signals early, mFilterIt helps advertisers protect budgets, improve performance accuracy, and scale campaigns with real users.
Know more about how mFilterIt ensures app fraud protection across every funnel stage
Way Forward
Click-to-install time mapping helps identify invalid installs at an early stage and take proactive action. However, the work doesn’t end there. Marketers need a continuous validation process to ensure invalid traffic is not impacting their campaign performance. CTIT can be your signal to identify the red flags, while an advanced ad traffic validation tool for mobile campaigns can be an additional layer of protection to ensure your ad campaigns are protected from ever-evolving ad fraud threats.
If you see any of these abnormal CTIT patterns, take action today to protect your ad campaigns. Connect with our ad fraud detection experts today!




