With the rapid growth in the mobile app ecosystem, the number of fraudulent activities is also increasing at the speed of lightning. From the installs to events, the fraudsters have become smart enough to tamper with these metrics and steal the advertiser’s money. One of the common and sophisticated types of mobile ad fraud is Click Injection.
Click Injection is a technique that not only impacts the advertisers but also the genuine publishers who are generating real traffic.
Here is a handy guide to know how click injection impacts your app and how the click injection rule can help combat this threat.
What is Click Injection?
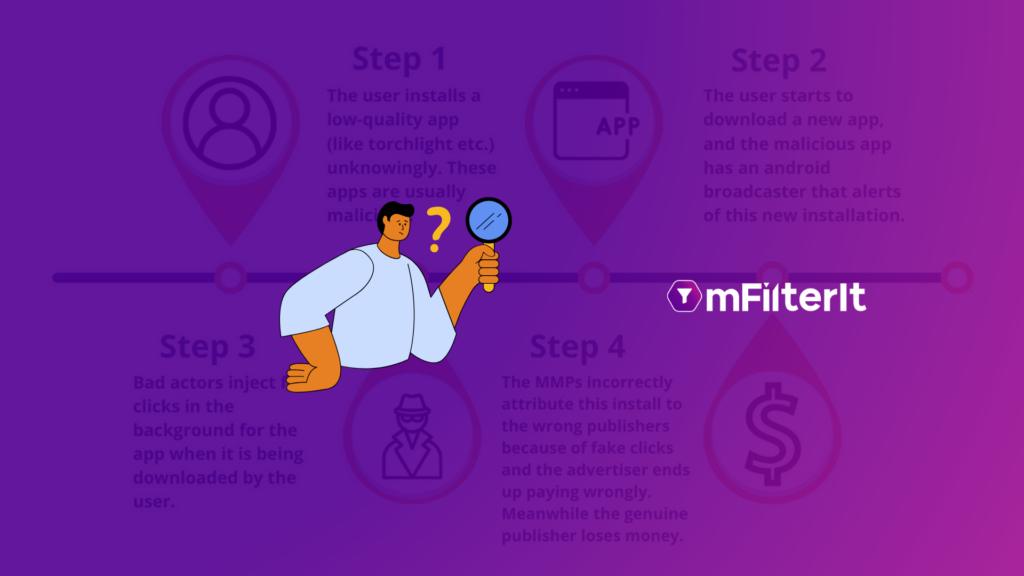
Click injection is a sophisticated form of mobile ad fraud that is used to manipulate app installs. It is a technique where a malicious app or a spoofed SDK in a user’s device fires an ad click between the duration of a genuine app download till it’s first open. The genuine publisher loses their payout as the last click is attributed to a fraudulent install.
How does Click Injection happen?

How mFilterIt Protect Against Click Injection?
Due to the last click attribution, the install is attributed to the publisher who has fired the last click on the advertisement. However, the fraudulent publishers steal the last click attribution by firing a click just before the app install completes.
To detect this anomaly, we apply our click injection rule which analyses the concentration of clicks by contributing publishers for a specific publisher in a day. And if the clicks by contributing publishers exceed 40%, then we analyze the time difference between the clicks (the time when the first click on the ad happened and the time when the contributor click happened)
If the click happens within a certain timeframe, then we mark it as fraud. To simplify this further, this pattern happens when the publisher is involved in a click-injection activity. Otherwise, the chances of this happening are minuscule.
These checks are conducted on three levels to get a deep-dive understanding of the anomalies in the installs and give transparency to the advertisers to evaluate their ad traffic quality.
Real Case
To explain this better, we have taken an example of a publisher who was actively involved in these kinds of activities.
We observed the installs from this particular publisher for a period of 15 days in which he gave 11,917 installs out of which 6,434 installs were contributed by other publishers or came organically. This consisted of 54% of the total traffic. According to the click injection rule, we marked all the records as a fraud whose difference was within a certain timeframe.
It’s Not All Black
There is a grey zone in the digital ecosystem. Not all contributing publishers are participants in mobile ad fraud. Some of them are unaware of the fraudulent activities that happen within the app they publish or distribute. While there are some contributing publishers who are misled by fraudulent app developers or ad networks. This led to financial losses for not just the advertisers but the genuine contributing publishers as the fraudulent publishers steal their share of revenue by capturing the last-click attribution.
Way Forward
The fraudulent techniques in the digital ecosystem are becoming sophisticated and discreet with every passing day. Due to this, marketers are in a constant dilemma of choosing the right media partner to advertise with confidence. Therefore, validating the ad traffic from publishers and sub-publishers has become a necessity to ensure that there is transparency and trust among all parties. With the right ad traffic validation solution, marketers can get clarity on their ad traffic, and decide which channels they need to focus on to get greater returns.
Marketers, it’s time to leave the old ways and advertise fearlessly with a media partner you can trust!